Let's Encrypt Ends Certificate Expiry Emails – What Users Need to Know

Starting June 2025, Let's Encrypt will cease sending automated certificate expiration notifications to its users. This decision comes as part of a strategy to reduce costs and focus resources on more critical tasks. Many users have already automated their certificate renewal process, making these notifications less necessary.
Why Let's Encrypt is Changing Its Strategy
Let's Encrypt representatives explained that the decision to discontinue automatic notifications was made for several reasons. Firstly, many clients have already automated certificate renewal, making additional reminders unnecessary. Secondly, sending these notifications costs the organization tens of thousands of dollars each year, and the developers believe these funds could be directed toward more important tasks.
"Sending emails with expiration notifications means we must store millions of email addresses associated with certificate records. As an organization that values privacy, we consider it very important to abandon this practice," added Let's Encrypt. "The process complicates our infrastructure, requires time and attention for support, and increases the chance of errors. In the long term, especially with new service components being added, Let's Encrypt aims to reduce the overall complexity of the system by gradually phasing out elements that no longer justify their existence."
Recommendations for Certificate Management
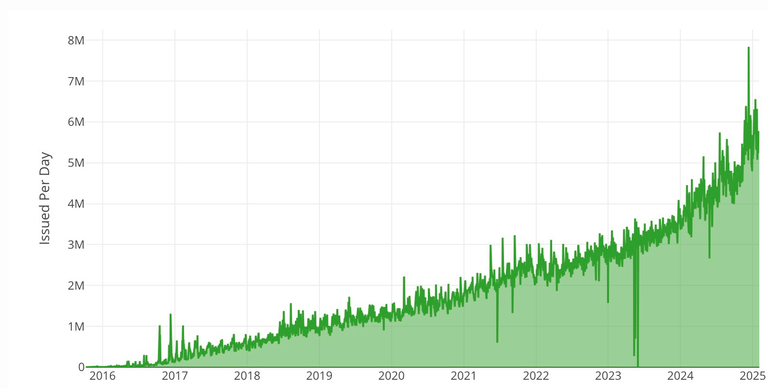
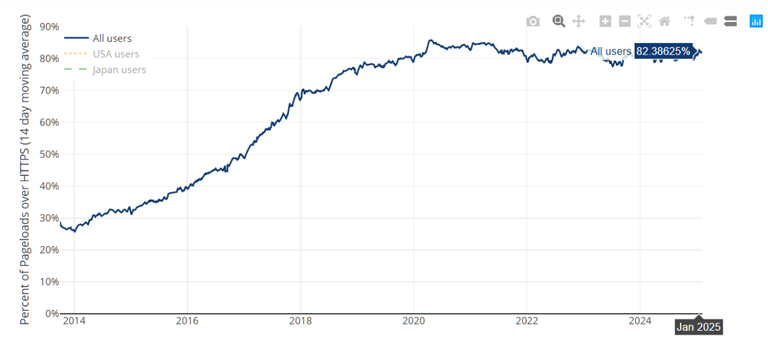
The organization recommends using Red Sift Certificates Lite for tracking certificate expiration (the service is free for up to 250 certificates). Other possible options include Datadog SSL monitoring and TrackSSL. According to Let's Encrypt's official statistics page, as of December 2024, approximately 8 million certificates were issued daily. The number of HTTPS-secured pages continues to grow steadily, surpassing 82% of the total as of January 2025.
The Growing Importance of Cybersecurity Awareness
VulnCheck analysts reported that in 2024, there were 768 CVEs recorded which were used by attackers in real-world attacks—20% more than in 2023 when hackers exploited 639 vulnerabilities.
Understanding CVE and KEV in 2024
Researchers noted that 23.6% of all known exploited vulnerabilities (KEVs) last year were used either on the day their CVEs were publicly disclosed or even before that point. This is slightly less than in 2023 (26.8%), and experts write that exploitation attempts can occur at any time during a vulnerability's existence, regardless of the hype surrounding zero-day bugs.
"In 2024, only 1% of publicly disclosed CVEs were used in real-world attacks. This number is expected to grow as exploitations are often discovered long after a CVE is disclosed," experts noted. At the end of last year, specialists also warned that about 400,000 internet-accessible systems might be vulnerable to attacks related to just 15 vulnerabilities in products from Apache, Atlassian, Barracuda, Citrix, Cisco, Fortinet, Microsoft, Progress, PaperCut, and Zoho. At that time, VulnCheck advised organizations to use reliable threat analysis tools, effectively manage patches, and minimize internet access for such devices whenever possible.
Sponsored
Sponsored
Sponsored
Explore More:

New Wave of Malware: Over 20 New macOS Threat Families Discovered in 2024
Renowned macOS security expert Patrick Wardle reported that over 20 new families of...
The Role of Interest Rates in Banking
Importance of Interest Rates in Banking Interest rates play a crucial role in...
How do banks facilitate payments and transfers?
Banks play a crucial role in facilitating payments and transfers for individuals and...
What services do banks offer to individuals and businesses?
Banks offer a wide range of services to both individuals and businesses. Some...
How do banks manage risks and ensure financial stability?
Banks manage risks and ensure financial stability through a variety of strategies and...
What is the role of central banks in the banking industry?
Role of Central Banks in the Banking Industry Central banks play a crucial...
What are the different types of banks and their functions?
Different Types of Banks There are different types of banks that serve various...
How does a bank operate and generate revenue?
How does a bank operate? A bank is a financial institution that offers...
What is the purpose of banking business?
The purpose of banking business is to provide financial services and facilitate the...

Definition of Banking
Banking is a fundamental and integral part of any economy. It plays a...
What are the current trends and challenges facing the banking industry?
Current Trends in the Banking Industry Digital Transformation: The banking industry is undergoing...
How do banks facilitate international trade and foreign exchange transactions?
Banks play a crucial role in facilitating international trade and foreign exchange transactions....
What is the importance of regulatory compliance in the banking sector?
Importance of Regulatory Compliance in the Banking Sector Regulatory compliance plays a crucial...
How do banks assess creditworthiness and make lending decisions?
Banks assess creditworthiness and make lending decisions using various methods and factors. Here...
What is the impact of technology on the banking industry?
Impact of Technology on the Banking Industry Technology has greatly transformed the banking...
How Do Banks Control Risks to Maintain Financial Stability?
1. Credit Risk Management Credit risk arises from the possibility that borrowers may...